Vulnerability assessments and penetration tests both provide valuable insight on vulnerabilities found within organizations and are important proactive tactics to help reduce the risk of a cyberattack. Because of these resemblances, vulnerability assessments are often confused with penetration tests. Although similar, the analysis of a vulnerability assessment and the simulated attacks of a penetration test are very different.
A vulnerability assessment looks at the organization as a whole and identifies attack paths and other vulnerabilities, while also laying out areas of opportunity that could be used to improve cybersecurity. Typically, a vulnerability assessment is performed before a penetration test. The assessment provides detailed information on vulnerabilities, sorted by severity. Those vulnerabilities get passed along to a remediation team, which can be in-house or a third party. During remediation, custom solutions get developed that implement controls to address the risk, while minimizing impact to the operations and maintenance departments. Once the findings from the vulnerability assessment have been remediated with controls in place to improve defenses, the next step is to verify everything is working as planned. This is where penetration testing comes in.
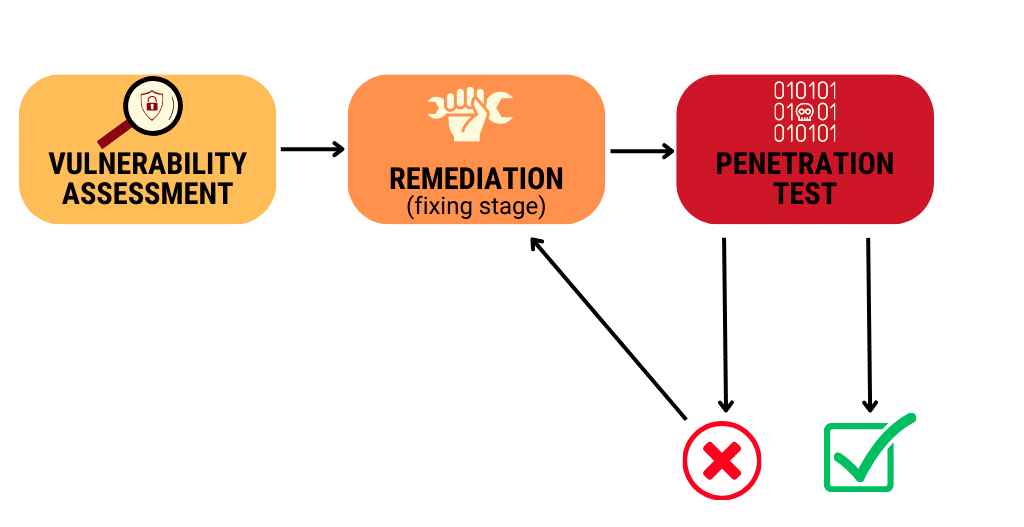
A penetration test uses ethical hackers to simulate a cyberattack against your network, system, or web applications and confirms the implemented solutions have indeed solved the problem. There are different types of penetration tests. The type that generally provides organizations with the biggest bang for their buck is one that is performed from the perspective of an attacker that already has access to the organization’s internal network infrastructure. This allows the organization to measure the potential impact of a perimeter breach or insider threat situation. For example, a common scenario might be to provide basic access into the corporate network and test whether it’s possible to move laterally within the environment to achieve Domain Administrator-level access.
Often, additional vulnerabilities get found during the penetration test. In these situations, those vulnerabilities, along with helpful details such as how to recreate the issue, get sent off to the remediation team. After remediation, the vulnerability gets tested again as the cycle continues until the vulnerabilities get solved.
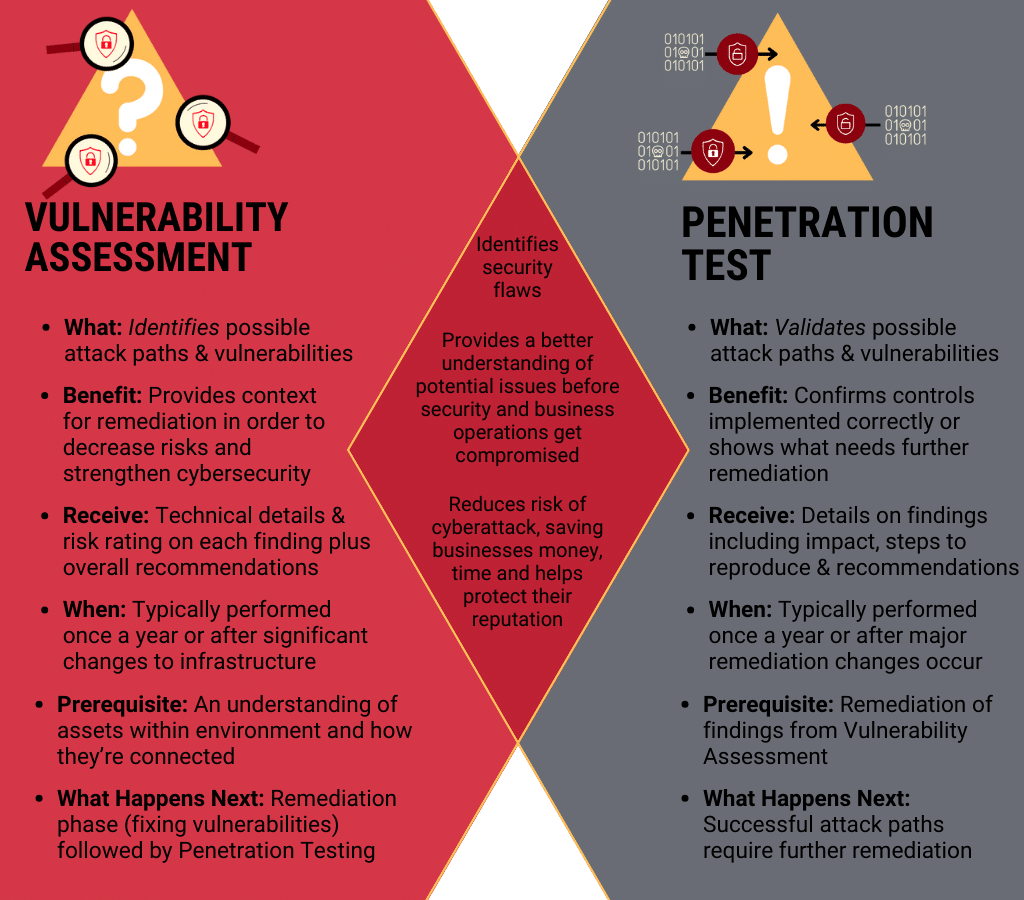
Essentially, the goal of a vulnerability assessment is to obtain a comprehensive overview of the environment and identify areas of opportunity for improvement to strengthen defenses. On the other hand, the goal of penetration testing is to test security controls and processes to understand how far a malicious actor could go in the event of a breach. Together, a vulnerability assessment and penetration test can tell you what is at risk and how it can be fixed so you can improve the overall security of your system.
For more in-depth information, check out the video presentation below

Learn the Following:
- Advantages and disadvantages of penetration tests, vulnerability assessments and vulnerability scanners
- How to determine whether a penetration test, vulnerability assessment or vulnerability scanner is right for you (and when)
- Automated tools vs manual tools


